CloudFront now Supports ECDSA Certificates for HTTPS Connections to Origins | Networking & Content Delivery

cryptography - Additional zero byte in RFC 5915 ECDSA public key generated by OpenSSL - Stack Overflow
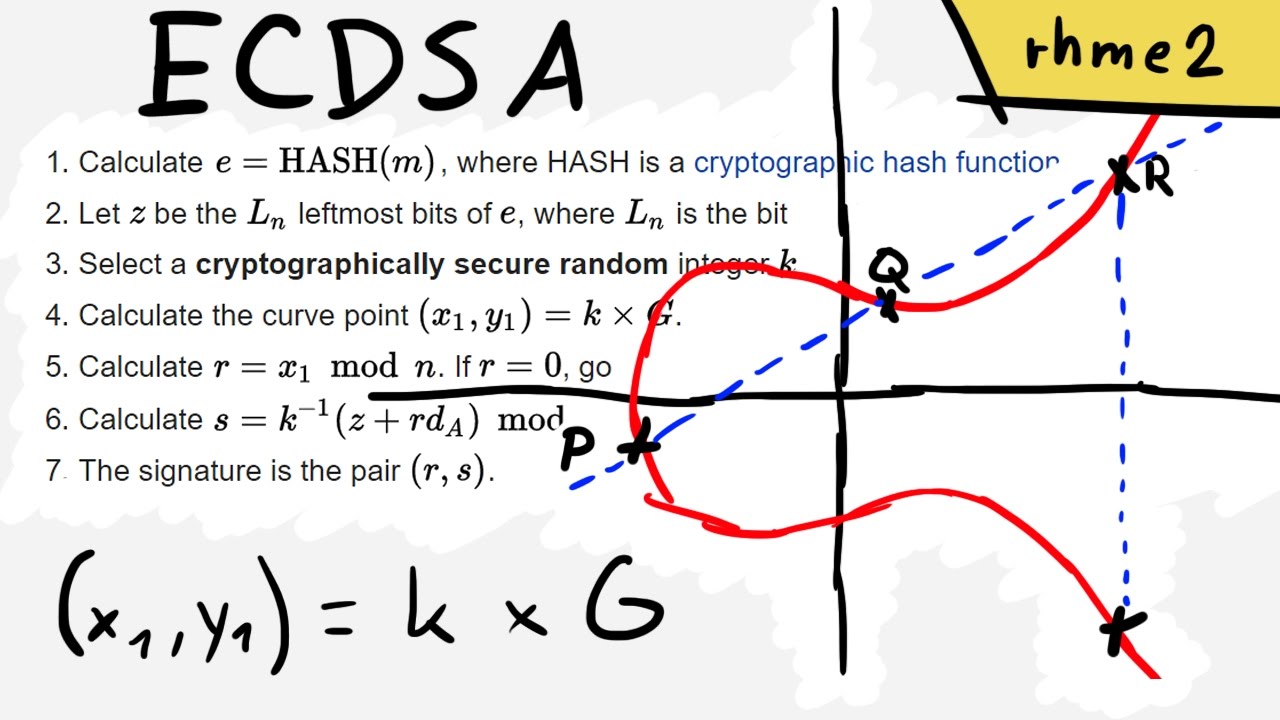
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150) - YouTube